Realm settings
On the left sidebar, click Settings, and then click one of the following tab.
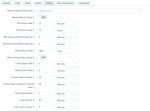
On the General tab, you perform the following actions.
| Item | Description |
|---|---|
| Name | View the name of the realm. |
Frontend URL | Specify the front-end URL for the realm: use it in combination with the default hostname provider to override the base URL for the front-end requests for a specific realm. Use case example: If you are deploying multiple clusters for high availability or balancing purposes, set the Frontend URL as the base URL used by the end users when accessing the application. Important: Setting an incorrect value might result in the platform’s inaccessibility. You can edit the value only in the master console of Access Manager. |
| Endpoints | View the configuration of the OpenID Connect endpoints by clicking the name link. |
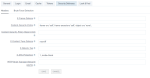
On the Login tab, you can define settings related to login and email if you are using local authentication. After you define the settings, ensure that you save the changes.
| Item | Description |
|---|---|
| User registration | If ON, users can register themselves. |
| Edit Username | If ON, users can edit their usernames. |
| Forgot password | If ON, user can restore forgotten password by clicking the respective link on the login page. |
| Remember Me | If ON, the Remember Me checkbox is added to the login page. By selecting this checkbox, users can remain logged even if the browser is closed until their session expires. |
| Verify Email | If ON, users must verify the email the first time they log in. |
| Log In with Email | If ON, users can log in with their email address. |
Require SSL | The SSL mode defines the SSL/HTTPS requirements for interacting with the realm. Browsers and applications that interact with the realm must conform to the SSL/HTTPS requirements defined by the SSL mode. Otherwise, they will not be allowed to interact with the server. Select the SSL mode of your realm:
The Platform is not set up by default to handle SSL/HTTPS. We recommend that you enable SSL either on the server itself or on a reverse proxy in front of the server. |
The platform sends emails to users to verify their email address or to notify an administrator of a server event. To enable the platform to send emails, you need to provide your SMTP server settings. This is configured for the whole realm on the Email tab.
The following table provides details related to the SMTP server settings to be specified. After you define the settings, ensure that you save the changes.
| Item | Use this item to |
|---|---|
| Host | Enter the SMTP server hostname used for sending emails. Click Test Connection to verify the connection. |
| Port | Enter SMTP server port number. This port is set to 25 by default. |
From Display Name | (Optional) Enter the user-friendly email address aliases. If not set, the plain From email address is displayed in email clients. |
| From | Enter the address used for the From SMTP-Header for the emails to be sent. |
| Reply To Display Name | (Optional) Enter the user-friendly name for the recipient’s email address. |
| Reply To | (Optional) Enter the address used for the Reply-To SMTP-Header for the mails sent. If not set, the From email address is used. |
| Envelope From | (Optional) Enter the email address for the bounce address that is used for the Return-Path SMTP-Header for the mails sent. |
Enable SSL | Select ON to enable Secure Sockets Layer. |
| Enable StartTLS | Select ON to enable StartTLS (an email protocol command that tells an email server that an email client, including an email client running in a web browser, wants to turn an existing insecure connection into a secure one). |
| Enable Authentication | If your SMTP server requires authentication, select ON and specify the credentials (username and password). |
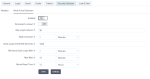
On the Tokens tab, you can define the following OpenID Connect token settings.
| Item | Description |
|---|---|
Revoke Refresh Token | If ON, refresh tokens can be used only once. If OFF, refresh tokens are not revoked when used and can be used multiple times. |
SSO Session Idle | The time during which a session can be idle before it expires. When a session expires, tokens and browser sessions are invalidated. The default value is 30 minutes. |
SSO Session Max | The maximum time during which a user session can remain active, regardless of activity. When the session expires, tokens and browser sessions are invalidated. The default value is 10 hours. |
Offline Session Idle | The time during which an offline session can be idle before it expires. An offline session will expire if you do not use an offline token to refresh at least once within this period. The default value is 30 days. |
| Access Token Lifespan | The maximum time after which an access token expires. We recommend that this value be shorter than the SSO timeout. The default value is 5 minutes. |
Access Token Lifespan for Implicit Flow | The maximum time after which an access token that is issued during the OpenID Implicit Flow expires. We recommend that this value be shorter than the SSO timeout. There is no possibility to refresh the token during the implicit flow. That is why this is a separate timeout setting different from Access Token Lifespan. The default value is 15 minutes. |
Client Login Timeout | The maximum time during which a client must finish the access token protocol (the Authentication Code Flow). The default value is 1 minute. |
Login Timeout | The total time that a login must take. If the authentication takes longer than this time, the user will have to restart the authentication process. |
Login Action Timeout | The maximum time during which a user must perform all the actions related to login. The default value is 5 minutes. |
User-Initiated Action Lifespan | The maximum time during which an action permit sent by a user (for example, “forgot password” email) expires. We recommend that this value be short because the user is expected to react to self-initiated actions quickly. The default value is 5 minutes. |
Default Admin-Initiated Action Lifespan | The maximum time after which an action permit sent to a user by admin expires. We recommend that this value be long so that the admin can send emails to users that are currently offline. The default timeout can be overridden just before the token is issued. The default value is 12 hours. |
On the Security Defenses tab, you can define the following settings.
On the Headers subtab, you can change some default HTTP response headers set by Access Manager as needed.
| Item | Description |
|---|---|
X-Frame-Options | The default value is SAMEORIGIN. The default value prevents pages from being included via non-origin iframes. For details on this header, click the header link. |
Content-Security-Policy | The default value is frame-src 'self'. The default value prevents pages from being included via non-origin iframes. For details on this header, click the header link. |
X-Content-Type-Options | The default value is nosniff. The default value prevents Internet Explorer and Google Chrome from MIME-sniffing a response away from the declared content type. |
X-Robots-Tag | The header prevents pages from appearing in search engines. The default value is none. For details on this header, click the header link. |
X-XSS-Protection | This header configures the cross-site scripting (XSS) filter in your browser. The default value is 1; mode=block. If the default value is used, the browser will prevent rendering of the page when an XSS attack is detected. For details about this header, click the header link. |
HTTP Strict Transport Security (HSTS) | This header tells browsers to always use https. When the browser identifies this header, it will only visit the site over https for the time specified (1 year) at max-age, including the subdomains. |
On the Brute Force Detection subtab, you can turn on the brute force detection capabilities. A brute force attack happens when an attacker is trying to guess a user’s password. If the detection is turned on, a user account will be temporarily disabled if a threshold of login failures is reached.
| Item | Description |
|---|---|
Enabled | If ON, the brute force detection is turned on. |
Permanent Lockout | If ON, the account will be locked permanently if the user exceeds the maximum login failures. |
Max Login Failures | The maximum number of login failures within the time period specified in Failure Reset Time after which the account will be temporarily disabled. The disabling time is specified in Wait Increment. If the actual number of failures is larger than the maximum number specified, the disabling time (the Wait Increment value) should be multiplied by the number of failures over the maximum. |
Wait Increment | The amount of time during which the account will be temporarily disabled if the number of login failures within the time period specified in Failure Reset Time reaches the number specified in Max Login Failures. If the actual number of failures is larger than the maximum number specified, the Wait Increment value should be multiplied by the number of failures over the maximum. If Permanent Lockout is turned on, this setting is not available. |
Quick Login Check Milli Seconds | The number of subsequent login failures for one account that are too quick for a human to initiate after which the account will be disabled. |
Minimum Quick Login Wait | The amount of time during which the account will be disabled if there are subsequent login failures for the same account within the time period specified in Quick Login Check Milli Seconds. |
Max Wait | The maximum amount of time during which an account can be disabled. If Permanent Lockout is turned on, this setting is not available. |
Failure Reset Time | Specify the amount of time after which all failures are cleared. If Permanent Lockout is turned on, this setting is not available. |
The detection works in the following way: if there are 30 login failures during 12 hours, the account is temporarily disabled for 1 minute (multiplied by the number of failures over the max). After 12 hours, all failures are wiped. 15 minutes is the maximum amount of time during which an account can be disabled. Moreover, if there are subsequent login failures for one account that are too quick for a human to initiate, the account will be disabled. This is controlled by the Quick Login Check Milli Seconds value. So, if there are two login failures for the same account within 1000 milliseconds, the account will be disabled for 1 minute.
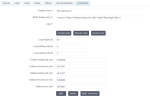
On the Look & Feel tab, you can customize the appearance of some user interface elements in the platform. After the edits on this tab, click Save to apply the changes. You can also revert the changes to the default settings.
| Item | Description |
|---|---|
Display name | Specify the realm display name. The display name (in uppercase) is used as a logo label if the HTML display name is empty, on the Login and Home pages of the platform. |
HTML display name | Specify the logo label or image with the HTML formatting. You can provide the link to the image and define the sizing. For example, <img src="https://www.yourwebsite.com/logo.png" style="width:90px;height:42px;">. The HTML display name is applied on the following pages of the platform:
|
Logo | Upload your logo or use a default one. You can control its size and padding by using the logo height and padding settings. If you delete the logo from this field, the HTML display name will be used. |
Logo height (px) | Specify the logo image height, up to 40 px. |
Logo padding top (px) | Specify the padding above the logo image. Move the logo within the toolbar area (the toolbar height is 42 px). |
Logo padding left (px) | Specify the padding to the left of the logo image. |
Toolbar background color | Specify the color for the top toolbar. |
Toolbar text and icon color | Specify the color for the text and icons on the top toolbar |
Sidebar background color | Specify the color for the left sidebar. |
Sidebar text and icon color | Specify the color for the text and icons on the left sidebar. |
Comments
0 comments