Configure SAML/OpenID Connect
Protocol-based providers are those that rely on a specific protocol to authenticate and authorize users. By using them, you can connect to any identity provider compliant with a specific protocol. It is easy to configure and broker any identity provider based on these open standards.
Although each type of identity provider has its own configuration options, all of them share some common configuration.
Procedure
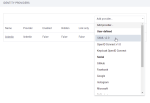
- In the Access Manager, on the left sidebar, click Identity Providers.
From the Add provider dropdown list, select an authentication protocol.
Note: The Keycloak OpenID Connect protocol is not described separately within this topic. This protocol is an OpenID Connect v1.0 protocol customized specifically for Keycloak. It shares all the settings that are configured for OpenID Connect v1.0 protocol.
The configuration page for the identity provider opens.
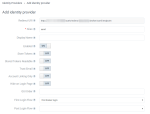
Specify the general settings for the identity provider.
 General settings
General settingsSetting Use this setting to Redirect URI Add the redirect URI that must be used when configuring the identity provider. Alias Add a unique alias that identifies the identity provider internally. The alias is also used to build the redirect URI. Display Name Add a name for the identity provider. This name is used in the table that lists all the configured identity providers. Enabled Enable or disable the identity provider for the users.
The default value is ON.
Store Tokens Specify whether the tokens should be stored after the user is authenticated.
The default value is OFF.
Stored Tokens Readable Specify whether users are allowed to read the stored tokens. This setting also applies to the broken.read-token role. The default value is OFF.
Trust Email
Specify whether the email provided by the identity provider is trusted or not. If you enable this setting, the email is not verified even if verification is enabled for the realm.
The default value is OFF.
Account Linking Only
Specify whether users can log in with this identity provider or can only link to it. If you enable this setting, users are not allowed to log in with the provider; their accounts are integrated with the provider.
The default value is OFF.
Hide on Login Page
Hide or show the identity provider on the login page.
If you enable this setting, users can log in with this provider only by requesting it explicitly, for example by using the kc_idp_hint.
The default value is OFF.
GUI Order Add a number that defines the order of the provider on the login page or other graphical user interface (GUI). First Login Flow
Select the authentication flow that is triggered for users who log in to the Platform with the identity provider for the first time. “For the first time” means that the user does not yet have an existing Platform account linked with the authenticated identity provider account. Post Login Flow Select the authentication flow that is triggered after the users log in with the identity provider. Use this setting if you want additional verification of each user authenticated with this identity provider. Please note that the user should be already set in ClientSession as the identity provider already set it. Specify the settings for the external identity provider and for the service provider.
 Settings for identity providers that use SAML v2.0
Settings for identity providers that use SAML v2.0Setting Use this setting to Single Sign-On Service URL Add the URL that must be used to send authentication requests (SAML AuthnRequest). If the identity provider publishes an entity descriptor, the URL is specified in this descriptor. Single Logout Service URL Add the URL that must be used to send logout requests. If the identity provider publishes an entity descriptor, the URL is specified in this descriptor. Backchannel Logout Specify whether the identity provider supports a backchannel logout. The default value is OFF. NameID Policy Format Specify the URI reference that corresponds to a name identifier format. The default value is Persistent (urn:oasis:names:tc:SAML:2.0:nameid-format:persistent). HTTP POST Binding Response Specify whether the HTTP POST binding should be used for responding to requests that are sent by the identity provider. If this setting is set to OFF (the default value), the HTTP Redirect binding is used. HTTP POST Binding for AuthnRequest Specify whether the HTTP POST binding should be used for sending an authorization request (AuthnRequest). If this setting is set to OFF, the HTTP Redirect binding is used. HTTP POST Binding Logout
Specify whether the HTTP POST binding should be used for responding to logout requests. If this setting is set to OFF, the HTTP Redirect binding is used. Want AuthnRequests Signed
Specify whether the identity provider expects a signed AuthnRequest. If this setting is set to ON, the AuthnRequest is signed by using a key pair of the realm. Want Assertions Signed
Specify whether the identity provider expects a signed assertion. Want Assertions Encrypted Specify whether the identity provider expects an encrypted assertion. Signature Algorithm
Select the algorithm of the signature that you want to be used for signing documents. This setting is visible only if Want AuthnRequests Signed is set to ON. SAML Signature Key Name Select the name of the signature key. This name appears in the KeyName element of signed SAML documents. This setting is visible only if Want AuthnRequests Signed is set to ON. Signature Algorithm
Select the algorithm of the signature that you want to be used for signing documents. This setting is visible only if Want AuthnRequests Signed is set to ON. SAML Signature Key Name Select the name of the signature key. This name appears in the KeyName element of signed SAML documents. This setting is visible only if Want AuthnRequests Signed is set to ON. Force Authentication
Specify whether the identity provider must force the users to their credentials, even if they are already logged in. If this setting is set to ON, the identity provider authenticates the users directly and does not rely on previous authentications. Validate Signature Enable or disable the signature validation for SAML responses. It is recommended that you set this setting to ON.  Settings for identity providers that use OpenID Connect v1.0
Settings for identity providers that use OpenID Connect v1.0Setting Use this setting to Authorization URL Add the authorization URL required by the OpenID Connect protocol. Token URL Add the token URL required by the OpenID Connect protocol. Logout URL Add the logout URL defined in the OpenID Connect protocol. Backchannel Logout Specify whether the identity provider supports a backchannel logout. Disable User info Enable or disable the User Info service of OpenID Connect. You can use this service to get additional user information. User Info URL Add the User Info URL defined in the OpenID Connect protocol. Client ID Add the client or client identifier that is registered within the identity provider. The client ID is required when the Authorization Code Flow is used to interact with the identity provider. Client Secret Add the client secret that is registered within the identity provider. The client secret is required when the Authorization Code Flow is used to interact with the identity provider. Issuer Add the identifier of the response issuer. Responses from the identity provider may contain an issuer claim. If this setting is set to ON, the claims are validated against the value that you add. Default Scopes Add the OpenID Connect scopes that must be sent with the authorization request. If you need to enter multiple scopes, use spaces to separate them. The default value is openid. Prompt Select a prompt parameter. Validate Signatures Enable or disable the signatures validation for the identity provider. Use JWKS URL Enable or disable the downloading of the identity provider's public key from the URL that is added in the JWSK URL field. If this setting is set to ON, the public key and its updates are always downloaded from that URL. This setting is visible only if Validate Signatures is set to ON. JWKS URL Add the URL where the public and private keys of the identity provider are stored. This setting is visible if both Validate Signatures and Use JWKS URL are set to ON. Validating Public Key Add the public key in PEM format that must be used to verify the signatures of the identity provider. This setting is visible if Validate Signatures is set to ON and Use JWKS URL is set to OFF. Validating Public Key ID Add the ID of the public key that must be used to verify the signatures of the identity provider. If you leave this field blank, the validating public key added to Validating Public Key is used for all the requests, regardless of the key ID specified by the identity provider. If you add a value, this value must match the key ID specified by the identity provider. This setting is visible if Validate Signatures is set to ON and Use JWKS URL is set to OFF. Save your changes.
The identity provider is added to the list of identity providers.
(Optional) To edit the identity provider, in the list of identity providers, click its link or click Edit.
The configuration page for the identity provider opens. Do the following:
- Edit the settings as needed.
Save your changes.
- (Optional) To delete the identity provider, in the list of identity providers, click Delete, and then click Delete in the confirmation message.
Comments
0 comments