Configure LDAP/AD as an authentication provider
In Access Manager, you can configure LDAP/AD to be an authenticator for users in the Platform.
- On the left sidebar, click Authentication Providers.
In the dropdown list, select ldap as the provider type.
The LDAP configuration page opens.
Specify the settings as appropriate. Use the following tables to get details on the settings and recommended input for the Platform.
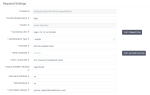
 Required Settings
Required SettingsSetting Use this setting to Examples and recommended input Console Display Name Specify a name used when this LDAP provider is referenced in the admin console.
For example, Active Directory
Vendor Specify the name of the LDAP provider.
Select Active Directory. Connection URL
Specify the connection URL to the LDAP server.
You can verify the URL by clicking Test connection next to this field.
Example:
ldap://10.15.16.3:389
Authentication Type Specify an LDAP authentication type.
Select simple to bind credential and bind password authentication. Bind DN Specify the DN of the LDAP admin to access LDAP server in the Platform. Example:
platform\admin
Bind Credential Specify the password of the LDAP admin.
You can verify credentials by clicking Test authentication next to this field.
Example:
AdminPassword789
Users Lookup DN Specify the full DN (distinguished name) of the LDAP tree where your users are stored. This DN is a parent of the LDAP users.
Example:
- ou=users,dc=example,dc=com (assuming that your typical user has the DN like “uid=john,ou=users,dc=example, dc=com”)
- ou=SBSusers,ou=Users,ou=MyBusiness,
dc=Platform,dc=local
Unique Identifier Attribute
Specify the name of the LDAP attribute that is used as a unique object identifier (UUID) for objects in LDAP.
Examples:
- entryUUID
- objectGUID (for Active Directory)
If your server does not support the UUID, use any other attribute that is unique among LDAP users in the tree like uid or entryDN.
Username Attribute
Specify the name of the LDAP attribute that is mapped as the username in the Platform.
This attribute must be specified for all the users that you want to import from LDAP to the Platform.
Examples:
- uid (for LDAP vendors)
- sAMAccountName (for Active Directory)
- cn (for Active Directory)
RDN attribute
Specify a name of the LDAP attribute that is used as an RDN (top attribute) of a typical user DN. Usually it is the same as the Username LDAP attribute.
For Active Directory, it is common to use cn if a username attribute is sAMAccountName. User Object Classes Specify all the values of the LDAP objectClass attribute divided by comma.
Existing LDAP users are found only if they have all those object classes.
Example:
- inetOrgPerson
- organizationalPerson
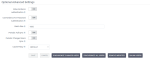
 Optional Common Settings
Optional Common SettingsSetting Use this setting to Examples and recommended input Custom User LDAP Lookup Filter Specify an additional LDAP filter when searching for a user. The filter is placed within parentheses. Leave empty if you do not need an additional filter. Search Scope Specify the search scope:
- One Level (the system will search for users in DNs)
- Subtree (the system will search for users in the whole subtree)
Select Subtree. Connection Pooling Specify whether the Platform should use connection pooling to access LDAP server. Select ON. Connection Timeout Specify the time in milliseconds for the connection timeout. For example, 3000. Read Timeout Specify the time in milliseconds for the LDAP READ timeout, which applies to LDAP read operations. For example, 3000. Pagination Specify whether the LDAP supports pagination. Select ON.  Optional Advanced Settings
Optional Advanced SettingsSetting Use this setting to Examples and recommended input Allow Kerberos authentication Specify whether to use HTTP authentication of users with SPNEGO/Kerberos tokens. The data about authenticated users will be provisioned from this LDAP server. OFF is selected by default. Use Kerberos for Password Authentication Specify whether to use the Kerberos login module for authenticating the username and password against the Kerberos server instead of authenticating against the LDAP server with Directory Service API.
OFF is selected by default. Batch Size Specify the number of LDAP users to be imported from LDAP to the Platform within a single transaction. 1000 is set by default. Periodic Full Sync Specify whether to set a periodic full synchronization of LDAP users to the Platform.
If you decide to use full synchronization, specify the period (in seconds) in the Full Sync Period field.
OFF is selected by default. Periodic Changed Users Sync Specify whether to set a periodic synchronization of changed or newly created LDAP users to the Platform.
If you decide to use this synchronization, specify the period (in seconds) in the Changed Users Sync Period field.
OFF is selected by default. Cache Policy Select the cache policy:
- DEFAULT
- EVICT_DAILY to delete user cache daily at a specific time
- EVICT_WEKLY to delete user cache weekly at a certain time and day of the week
- MAX_LIFESPAN to delete cache entry when its lifespan (in milliseconds) is over
- NO_CACHE
If appropriate, select another cache policy for this provider, and specify additional parameters when needed. By default, the default settings for the global user cache are selected. Click Save.
If the provider is successfully created, click the Synchronize all users button that appears to the right.
Wait for the confirmation message to verify that all the needed users are imported.
You can map LDAP user attributes into the Platform common user model. By default, the system maps username, email, first name, and last name, but you can configure additional mappings. If you need to configure the mappers, go to the Mapper tab of this configuration page. For details, see Configure LDAP mappers.
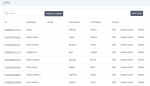
View the imported users on the Users page.
Comments
0 comments